Personnel Management
 ANSI/HL7 V3 PM, R1-2005 HL7 Version 3 Standard: Personnel Management, Release 1 10/28/2005 |
| Responsible Group | Personnel Management Work Group HL7 |
| Co-Chair | Leon Salvail lsalvail@global-village.net Global Village Consulting Inc. |
| Co-Chair | June Rosploch june.rosploch@kp.org Kaiser Permanente |
| Modeling & Methodology Facilitator | Robert B. Grant robert.b.grant@gov.bc.ca British Columbia Ministry of Health Services |
| Publishing Facilitator | Helen Stevens helen.stevens@gpinformatics.com Gordon Point Informatics Inc. |
HTML Generated: 2012-08-31T12:11:09
Content Last Edited: 2010-05-08T12:30:03
HL7® Version 3 Standard, © 2005 Health Level Seven® International All Rights Reserved.
HL7 and Health Level Seven are registered trademarks of Health Level Seven International. Reg. U.S. Pat & TM Off.
Use of these materials is governed by HL7 International's IP Compliance Policy.
Table of Contents
Preface
i Notes to Readers
ii Acknowledgements
iii Changes from Previous Release
iv Known Issues & Planned Changes
v Message Design Element Navigation
1 Overview
1.1 Introduction & Scope
1.2 Domain Analysis Model
1.3 Domain Information Models
2 Provider Registry Topic
2.1 Introduction
2.2 Storyboards
2.3 Application Roles
2.4 Trigger Events
2.5 Refined Message Information Models
2.6 Hierarchical Message Descriptions
2.7 Interactions
3 Organization Registry Topic
3.1 Introduction
3.2 Storyboards
3.3 Application Roles
3.4 Trigger Events
3.5 Refined Message Information Models
3.6 Hierarchical Message Descriptions
3.7 Interactions
4 Quality Analysis Report Topic
5 CMETs Defined by this Domain
6 Interactions Annex
6.1 By Application Role
6.2 By Trigger Event
6.3 By Message Type
7 Glossary
The committee is indebted to the following past co-chairs and facilitators for their contributions towards the Personnel Management Committee and the material presented here.
- Jean Spohn, Group Health Cooperative
- Charles Mead, M.D. MSc, Oracle Corporation - Healthcare
- Bernd Blobel, Fraunhofer Institute for Integrated Circuits - Health Telematics Project Group
- Frank Oemig, Ringholm GmbH Integration Consulting
It also expresses appreciation to the following developers and editors who contributed many days to prepare this publication:
- Lloyd McKenzie, LM &A Consulting Ltd.
- Scott Robertson, Kaiser Permanente
- Rene Spronk, HL7 Netherlands
- Isobel Frean, HL7 Australia
- Heidi Mabatid, DOD-MHS
- June Rosploch, Kaiser Permanente
The following non-substantive changes have been made since this domain was balloted and approved at a membership level:
- .
Harmonization Proposals:
The following harmonization proposals are pending:
- Add "GRNT" participation typecode code as leaf concept under ParticipationType. Concept code "GRNT".
- Print name: Grantor
- Definition: A entity (person or organization) with primary responsibility for conferring privileges.
- Example: Medical practice privileges are granted to a HealthCareProvider by a hospital Board.
- Rename ControlProcessId to ControlActReferenceId. The name change has not yet been incorporated into this domain's models however it is referenced in the Control Act Event description in the DMIM walkthrough.
Model Changes:
- Model changes are planned to sections of the DMIM having to do with role verification. These changes will harmonize the DMIM with the new draft-for-comment cmet COCT_RM810000 that has been included in the Common Domains chapter of this publication. The affected portions of the DMIM are unrelated to the material that has been released for membership ballot at this time.
|
||||||||||||||||||||||||||||||
|
Scope
The Personnel Management Domain spans a variety of clinical-administrative information functions associated with the organizations, individuals, animals and devices involved in the delivery and support of healthcare services. The domain content includes roles, relationships, credentials, certificates, licenses, capacities, capabilities, competencies, qualifications, privileges, responsibilities, and assignments issued to or managed by the involved organizations, individuals, animals and devices.
The PM Domain assumes the responsibility for communicating specific data associated with the domain content including status, coded names, demographic details, participating parties, activation and termination dates, and associated supporting documentation.
Introduction
The Personnel Management Domain is organized into four Topic Areas; Provider (Registry), and Organization (Registry). The Human Resources (HR) and Regulatory (both clinical and administrative) topics differ fundamentally in the amount of detail exposed relative to a given context relationship. As a consequence, the PM Domain's messages support a range of detail, from basic existence (e.g., a provider is recognized by an organization) to highly detailed (e.g., credentialing management).
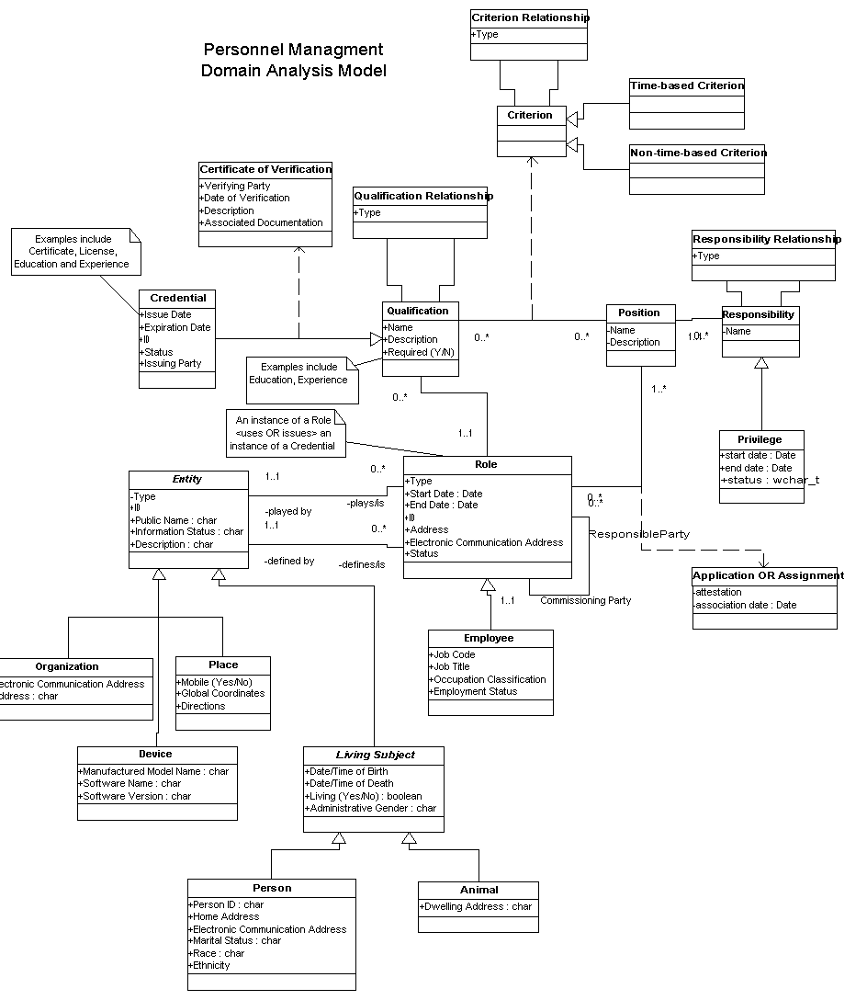
The Personnel Management Domain Analysis Model
The following Domain Analysis Model (DAM) was developed by the personnel management committee as part of the exercise of modeling the business of Personnel Management. This same business information is in turn reflected in the Domain Information Model (DMIM), where needed to fulfill messaging requirements. The purpose of the DAM is to show the relationships between the significant classes in the domain and the key attributes of interest within each class.
Concept DescriptionWithin the PM Domain, the term credential is defined as a token representing (or containing) the collection of data that attests to the existence of a Relationship involving two and only two parties, the Commissioning Party and the Responsible Party. As defined, a credential can be a certificate, a license, a diploma, a written verification of work experience, or other token issued by the Commissioning Party as a statement of the Responsible Party's competency, capability, or capacity.
In the HL7 RIM this kind of relationship is expressed as a Role wherein the Commissioning Party is referred to as the Scoper (Scoping Entity) and the Responsible Party is referred to as the Player (Playing Entity). A Role is assumed by the Player (usually for a finite period of time) in the context of some sort of oversight by the Scoper. The Role may exist independently from the existence of a Credential (or Credentials); however, if Credential(s) exists they are regarded as a description or attribute of the Role.
Thus, within this framework, the term 'credential' can be used to attest to the existence of relationships (Roles) in any number of contexts and degrees of formality. This includes the processes associated with, and connotations applied to, the terms license, certificate, education, work experience, capability, capacity, competency, qualification, etc.
Example: The Jurisdictional Medical Board defines the set of competencies and time constraints associated with the role of "Licensed Physician". The Board assigns this role to a specific person thus establishing a "Licensed Physician" relationship with that person and subsequently issues a license as evidence of the relationship. Thus the Role and the Relationship defining it are synonymous. The HL7 RIM represents the Medical Board as the Scoping Entity (Organization), Licensed Physician as the Role and the designated person as the Playing Entity (Person).
Following is a full walkthrough of the DAM diagram.
Domain Analysis Walkthrough
The Personnel Management Domain Analysis Model (DAM) represents the central concepts, attributes, and relationships that define the domain(s)-of-interest of the Personnel Management Technical Committee (PM TC) using the iconography of UML class diagrams. The development of a DAM for a given domain is described in the Requirements and Analysis chapter of the Health Development Framework (HDF) process being developed by HL7.
An initial version of the PM DAM was built over the course of two Working Group meetings in 2003 using input from a variety of domain experts from Human Relations (HR), regulatory agencies, and US Department of Defense Credential and Credential/Privilege Management. It has subsequently been (and will continue to be) expanded/more finely granulated based on ongoing discussions with numerous domain experts including those working on specific projects such as Provider Registries, Credentialing and Privileging Systems, etc.
The DAM intentionally utilizes 'non-RIM-speak' (i.e. terms familiar to domain experts but not necessarily used in the RIM) to capture the essential concepts, attributes, and relationships of the domain in 'domain-friendly' terms. In the best-of-all-possible worlds, the DAM would reach a fairly mature state before it would be utilized as a guide to construct a semantically equivalent PM DMIM. In fact, the PM TC had an existing DMIM before they committed to adopting the HDF and, as a consequence, building a DAM. As such, the DAM is being simultaneously developed in both a forward (DAM -> DMIM) and backward (DMIM -> DAM) direction.
A listing of the Domain Analysis Classes is included below to provide a glossary critical to the successful understanding of the mapping between the DAM and DMIM that explains the semantic equivalence between the two representations.
The central conceptual idea represented in the PM DAM is that of an instance of an Entity playing/assuming a Role. Note that Entity is an abstract concept, i.e. there are no instances of the Entity concept, but instead instances of the various subtypes of Entity, i.e. Place, Organization, Device, and Living Subject (which, in turn has subtypes of Person and Animal).
A specific Role may require certain Qualifications (which may be bundled together in complex collections whose semantics are specified by instances of Qualification Relationship) of the Entity subtype instance playing the Role. The specific Qualification of the 'playing' Entity instance may be validated by the 'assigning' Entity instance by one or more Credential instances issued to the playing Entity. Credential is modeled as a specialization of the concept of Qualification to distinguish that a Qualification is simply an assertion, whereas a Credential involves two Parties: a Responsible Party (the receiver of the credential) and a Commissioning Party (the issuer of the credential). These two concepts are currently not shown in the DAM but are conceptually represented in the PM DMIM by the relationships of Player and Scoper. Note that if a specific Credential is required for a particular Role, the scoping Entity (or other person or organization) may choose to validate the existence of the credential for the specific player Entity, capturing the details of this validation process in a Certificate of Verification.
An instance of an Entity-in-a-Role may apply for or be assigned to a Position, an action that is documented using an instance of the Application or Assignment class. Subsequent analysis as to the attributes of this class may dictate that it be split into two separate classes. A Position may be associated with one or more instances of the Responsibility class. Similar to the relationship between Qualification and Credential, the concept Responsibility is subtyped to Privilege, a type of Responsibility with a higher degree of formality in that it involves a 'contract' between the Privilege Grantor and the Privilege Recipient (concepts not currently shown in the DAM but similar DMIM concepts of Player and Scoper as discussed above). The DAM does NOT show that a Privilege may be granted to a Entity-in-a-Role in the absence of a formal assignment to a Position although this business process is often supported. This additional association is not shown because the details of any differences in messages required to support this concept are as yet unknown and uncertain. Finally, note that a Position may be associated with a complex set of Criterion instances which specify the set of Qualification and/or Credential instances and their inter-relationships in the context of a specific Position. The Criterion class has been subtyped to Time-Based Criterion and Non-Time-Based Criterion based on domain expert input. However, to date, little analysis has been done with respect to these concepts.
Domain Analysis Classes (Glossary)
The purpose of this Glossary of the Domain Analysis Model (DAM) Classes is to define the various concepts and attributes identified in the DAM and not, per se, to express the semantics of the DAM in terms of the RIM or its various derived artifacts. In particular, the final semantics of such mappings, although variously indicated or implied in the Glossary definitions and/or examples, may not be ultimately specified and/or unambiguously defined until the concept/attribute is included in one of the various 'down-stream' RIM-based artifacts (e.g. DMIM, RMIM, CMET, etc.)
NOTE: For attributes of each of the DAM concepts (classes), the current DAM has not made any attempt to rigorously specify either the type or the multiplicity of an attribute. Such specifications obviously become critical during the construction of the semantically equivalent (or nearly equivalent) DMIM and/or in the mapping of specific DAM concepts/attributes/relationships to the PM DMIM
Entity: A thing (or group of things) of interest in the PM Domain. The abstract superclass of Place, Organization, Device, and Living Subject containing the attributes common to all of these (concrete) subtypes. Examples: N/A
- Entity.Type: A coded description of the semantics of an instance of an Entity subtype. The coded description may simply point to one of the concrete Entity subtypes or, alternatively, describe an additional subtype whose existence does not require the creation of a concrete Entity subtype
- Entity.ID: A unique identifier for an instance of an Entity subtype
- Entity.Public Name: A text string by which an Entity subtype instance is known. An instance may have zero-to-many values for its Public Name attribute; the values are not considered to be unique, i.e. this is not a computable string
- Entity.Information Status: A named stage in the business lifecycle of the information for a given subtype of Entity, specifically Active, Inactive, or Nullified.
- Entity.Description: A text string which defines, explains, or otherwise clarifies the semantics of an Entity subtype instance from the perspective of a human reading the text string, i.e. this is not a computable string
Place: A physical location. Examples: physical boundaries specified by GPS coordinates
- Place.Mobile (Yes/No): An indicator set according to whether a named place is stationary or mobile.
- Place.GPS Coordinates: An n-tuple which specifically identifies a physical location in space.
- Place.Directions: One or more text descriptions of how to get from a particular location or region to the named place.
Organization: A formalized group of persons with a common purpose (e.g. administrative, legal, political, etc.) and infrastructure necessary to achieve said purpose. Examples: Joint Commission for Accreditation of Healthcare Organizations (JCAHO), Province of British Columbia, California State Board of Medical Examiners. NOTE: if an Organization is recognized from the perspective of one or more authorities and/or other organizations external to the Organization-of-Interest including legal, social, etc., the Organization is most likely an instance of the Entity subtype Organization playing a role recognized by (i.e. scoped by) another Organization instance.
- Organization.Electronic Communication Address: A specification of an numeric or string code by which a person may be contacted electronically. Examples: telephone #, email address, pager #, fax #
- Organization.Address: A string or number which specifies the location(s) at which an organization is physically located (an organization may have zero or more home addresses)
Device: A manufactured product used to provide medical services. Some of these complex products need to be certified as to the function performed. Examples: MRI machine, ECG monitor, arterial blood gas analyzer.
- Device.Manufactured Model Name: A numeric or character string assigned to a device by the device's manufacturer to differentiate the product from other products produced by the same manufacturer. Examples: Dell Latitude, Ford Taurus
- Device.Software Name: A character string given by the developer of a software product to a specific software product/collection of products. Examples: Windows NT, Quicken
- Device.Software Version: A character or numeric string assigned by the developer/developing organization of a specific software product to a particular instance of the software product which denotes the temporal (and often functional) sequencing of an instance of the software product in the overall lifecycle/evolution of the software product. Examples: v2.01, R3.6.4M
Living Subject: A biologically identifiable thing of interest in the PM . The abstract superclass of Person and Animal containing the attributes common to all of these (concrete) subtypes. Examples: N/A
- Living Subject.Date/Time of Birth : A character string denoting at an arbitrary level of detail the point in time at which a person or animal was born.
- Living Subject.Date/Time of Death : A character string denoting at an arbitrary level of detail the point in time at which a person or animal ceased to be alive.
- Living Subject.Living (Yes/No) : An indication as to whether a person or animal is alive or deceased.
- Living Subject.Administrative Gender : A non-biologically-based code describing the outward appearances of a person or animal for the purposes of non-reproductive tasks (e.g. accommodation assignment). Examples: male, female, unknown
Person: A subtype of Living Subject representing a single human being who, in the context of the PM Domain, must also be uniquely identifiable through one or more ID numbers/strings or legal documents (e.g. Driver's License, Birth Certificate, etc.) Example: John Smith (SS# 123-34-456)
- Person.Person ID : A string or numeric symbol(s) which uniquely define a particular person
- Person.Home Address : A string or number which specifies a location that a person indicates is their primary residence (a person may have zero or more home addresses)
- Person.Electronic Communication Address : A specification of a numeric or string code by which a person may be contacted electronically. Examples: telephone #, email address, pager #, fax #
- Person.Marital Status : A coded value describing a person's current status relative to a relationship defined under civil law as marriage, e.g. single, divorced, widowed, married
- Person.Race : A code describing a group of human beings distinguishable by genetic and/or phenotypic characteristics. Examples: Asian, Caucasian
- Person.Ethnicity : A code describing a collection of cultural and/or physical characteristics including but not limited to those used to characterize Race. Examples: Afro-American, Latino
Animal: A non-Person-of-interest to the PM Domain. In the PM Domain, an instance of an animal is uniquely identifiable and, as a result, able to be certified, licensed, or otherwise credentialed by an appropriate Credentialing Authority for the purpose of involvement in one or more healthcare processes. Examples: a German Shepard trained as a seeing-eye dog, a kitten licensed to a patient for comfort therapy
- Animal.Dwelling Address: The specified physical addresses at which a specific animal is located. In most cases, this address will be either that of the owner/person/organization responsible for the animal or the location in which the animal is currently providing healthcare services.
Role: A competency, capability, or capacity asserted or declared to be possessed by an instance of an Entity (the player or Responsible Party) and affirmed to be such (either implicitly or explicitly) by another instance of Entity (the scoper or Commissioning Party). Note that the role-based competency/capability/capacity is nearly always time limited (e.g. employee since, licensed until etc.).
- Role.Type: A coded description of the semantics of an instance of a Role subtype. The coded description may simply point to one of the concrete Role subtypes or, alternatively, describe an additional subtype whose existence does not require the creation of a concrete Role subtype
- Role.Start Date: The date/time at which a Role was created/becomes active (from the perspective of the Commissioning Party).
- Role.End Date: The date/time at which a Role ceases or becomes invalid (from the perspective of the Commissioning Party).
- Role.ID: A unique identifier for an instance of an Role subtype
- Role.Address: The addresses at which an instance of an Entity in the named Role may be contacted, managed, etc..
- Role.Electronic Communication Address: A specification of a numeric or string code by which a person may be contacted electronically. Examples: telephone #, email address, pager #, fax #
- Role.Status: A named stage in the business lifecycle of an instance of a Role or one of its subtypes, i.e. specifically New, Active, Suspended, Terminated, or Nullified.
Employee: An instance of a Role with a specific relationship (Employment) between the Player (Employee) and Scoper (Employer).
- Employee.Job Code: An employer-defined categorization of work, used primarily for payroll/remuneration purposes and not necessarily indicative of an employee's specific work assignments, responsibilities and privileges. Jobclass codes are typically user-defined and may not be readily interpretable without detailed knowledge of the sender's classification system.
- Employee.Job Title: The organization-assigned name of the job held, for example, Vice President, Senior Technical Analyst
- Employee.Occupation Classification: A classification of kind-of-work typically based upon a recognized industry or jurisdictional standard. Occupation codes are intended primarily as work descriptions that are suitable for a multitude of public uses e.g., job matching, employment counseling, occupational and career guidance, and labor market information services.
- Employee.Employment Status: The state of an instance of an Employee, i.e. specifically New, Active, Suspended, Terminated, or Nullified.
Application or Assignment: Separate definitions are given to indicate that this portion of the model is still immature, having not yet undergone detailed domain expert analysis.
- Application: The collection of data (structured and unstructured) that a Person submits to an organization in the context of requesting or applying for/being assigned to a Position. (NOTE: An Application does NOT include the Person's Qualifications or various Credentials (which are represented explicitly elsewhere in the model), but is simply a signed or otherwise verified statement by the Person applying for the Position that the data submitted in the context of the application process (including the Person's Qualifications/Credentials) are complete, accurate, etc. An Attestation is normally date/time stamped.)
- Assignment: A collection of data documenting the association between an instance of a Party (normally a Person) and a Position. The minimal data in an Assignment are date/time of Assignment and Person/Organization making the Assignment. An Assignment also usually includes a time period after which the Assignment is invalid and must be redone if the association between the Person and the Position is to continue.
Qualification: The supertype of Credential. A statement of a specific capability, competency, and/or capacity which may either be asserted by, or required for, a Role or Assignment or Application for a Position. A Qualification is differentiated from a Credential by virtue of the fact that a Credential carries the requirement of both the assertion and the validation ('vetting') of the capability, competency, and/or capacity, whereas the Qualification is simply the assertion per se.
- Qualification.Name: One or more text strings which designate the Qualification from the perspective of either the Commissioning or Responsible Party playing/scoping the Role instance.
- Qualification.Description: One or more text descriptions of the named Qualification
- Qualification.Required (Y/N): Indicates whether a particular Qualification is required or not (decided by a Commissioning Party)
Qualification Relationship: The concept used to link related instances of Qualification
- Qualification.Type: A code denoting the semantics of the linkage between two Qualification instances. Example: subsumes, requires
Credential: The collection of data associated with a verifiable claim by a Person or Organization as to one or more skills, abilities, education, experience, etc. An instance of a Credential may be issued in conjunction with the creation/activation of a given Role instance (Responsible Party) by the issuer of the Credential (Commissioning Party). Examples: License, Certificate, Education, Experience
- Credential.Issue Date: The date a given Credential was issued to the Responsible Party by the Commissioning/Issuing Party
- Credential.Expiration Date: The date a given Credential held by a Responsible Party expires as determined by the Commissioning/Issuing Party
- Credential.ID: A string or number which identifies an instance of a Credential
- Credential.Status: A named stage in the business cycle of a Credential including New, Held, Cancelled, Active, Suspended, Obsolete, Nullified
- Credential.Issuing Party: The named person or organization (more commonly organization) with the authority to issue the Credential, i.e. the Commissioning Party for the Role.
Certificate of Verification A collection of data documenting that a specific instance of a Credential has been vetted/verified/validated in association with the requirement for that Credential for either an Assignment of a Party in a Role to a Position or the requirement for a particular instance of a Credential in order for a Party in a Role to qualify for a specific instance of a Privilege.
- Certificate of Verification.Verifying Party: The name of the Party (Organization or Person) who verified the existence/correctness of a given instance of a Credential in a given business context (e.g. Role activation, Position application or assignment).
- Certificate of Verification.Date of Verification: The date on which the vetting activity for a given Credential was accomplished/completed.
- Certificate of Verification.Description: A textual description of the verification process for a given Credential including persons/organizations contacted, observations made, etc.
- Certificate of Verification.Associated Documentation: A collection of other documents (i.e. documents in addition to the Credential per se that were gathered during the verification process.
Position: A named collection of various duties, Responsibilities, and/or Privileges. A Position may exist without a Person in a Role being Assigned to that Position, i.e. a Position can be created/defined in terms of the Qualifications (including various forms of Credentials that a Person must have to qualify for an Assignment to that Position). A Position is considered to be dependent on the existence of a Role because of the common domain perspective that a 'base' or 'functional' role (e.g. Staff Physician) is often necessary before the (e.g. person) in a given 'base/functional' role can be assigned to other roles (e.g. Chair of Department of Cardiology, Director of ICU, etc.).
- Position.Name: Text name of a given Position, usually defined by the Party (person or organization) that creates the Position and ultimately assigns a person to that Position.
- Position.Description: Text description of a given Position.
Responsibility: The supertype of Privilege. An activity for which the Responsible Party is required to do to the satisfaction, under the jurisdiction of, as an agent for the Commissioning Party.
- Responsibility.Name: Text name(s) for a given Responsibility
Responsibility Relationship: The concept used to link related instances of Responsibility
- Responsibility.Type: A code denoting the semantics of the linkage between two Responsibility instances. Example: contains, <rule/predicate>
Criterion: A rule which defines the manner in which a particular Qualification (including a Credential) or collections of Qualifications are associated with a given Position. An instance of a Criterion may be either a Time-based Criterion (e.g. <xxx> for at least 3 years) or a Non-time-based Criterion (e.g. certified as either an <x> or a <y>).
Time-based Criterion: A rule with one or more time-based input parameters/attribute descriptors, e.g. if more than 3-days, after 20 minutes, etc.
Non-time-based Criterion: A rule for which input parameters/attribute descriptors are not time-based, e.g. if X = 3, if either A or B, etc.
Criterion Relationship: The concept used to link related instances of Criterion
- Criterion Relationship.Type: A code denoting the semantics of the linkage between two Criterion instances. Example: contains, alternative to.
Privilege: A subtype of Responsibility that is differentiated by virtue of the fact that it is associated with specific instances of Credential rather than instances of Qualification. Although a Privilege may be associated with a Position (e.g. the Position of Attending Physician may be associated with Admitting Privileges), a Person in a Role may, in addition, apply for other Privileges outside the context of a named Role. Each application involves at least one other Party who must review the Person-in-a-Role's specific Credentials required in order for the Privilege to be granted. Requirements may be defined by the Granting Party and/or by external organizations. NOTE: A Privilege differs from a Responsibility in that the association/assignment of a Privilege to a Person-in-a-Role requires the interaction of at least two instances of Party, i.e. the Person-in-a-Role (who may or may not be in a Position) requesting the Privilege and the Person/Organization-in-a-Role granting the Privilege. In the sense that it requires a 2-Party interaction,' the concept Privilege is therefore similar to Credential.
- Privilege.Start Date: The date at which a given Privilege becomes effective according to the granting party (i.e. the Commissioning Party).
- Privilege.End Date Date: The date at which a given Privilege is suspended/invalid according to the granting party (i.e. the Commissioning Party).
- Privilege.Status: A named stage in the business cycle of a Privilege including New, Held, Cancelled, Active, Suspended, Obsolete, Nullified.
Diagram
This model contains some 'placeholder' classes, derived from the Domain Analysis Model and having only minimal attributes at present; these are noted as placeholders below. The PM Committee has derived RMIM's for the Provider and Organization Topics from this DMIM and is currently working on models for the Human Resource and Regulatory Topics. This DMIM also supports all CMETs derived from this domain.
The committee developed this DMIM using several sources of information and input:
- Requirements drawn from v2.5, Chapter 15. Detailed segment mappings were completed between the v2.5 fields and v3.0 attributes in the DMIM. Mappings appear on the DMIM Diagram as attribute notations in parenthesis. For example: Employee.id (STF.2). Mapping details are published on the committee's website.
- The DMIM incorporates the two CMETs E_Organization[Universal] and R_AssignedEntity [Universal] CMETs that were developed prior to this DMIM.
- Requirements drawn from The Netherlands Organization Registry project
- Requirements drawn from the Canadian Provider Registry projects.
This walkthrough of the Personnel Management DMIM begins with a high-level overview of some of the principal features of the model. Following that are descriptions of entry points and interactions that are supported by the model. The overview concludes with an alphabetical listing of class objects in the DMIM and details of their use.
DMIM Overview
The scope of the Personnel Management Committee's domain includes the management of information regarding People, Organizations, Animals and Devices. The "Principal Choice" choice box at the bottom center of the diagram models these entities and the information directly related to them such as demographics, affiliations and language.
Of equal interest to the Committee is management of information regarding the various roles that may be played by these entities and lifecycle changes of the roles themselves.
A central feature of the DMIM is a discrete collection of Roles that are of particular interest in the PM domain and may (with some restrictions) be played by persons, organizations, animals or devices. These roles are present in the choice box entitled "Role Choice", which is also the primary entry point for RMIMs derived from this domain model.
Roles are relationships involving two parties: a player and a scoper. As already noted the player of these 'focal' roles may be different kinds of entities. Conversely, each of these roles is scoped solely by an Organization Entity, which appears just above the RoleChoice box in the diagram.
Lifecycle processes for Roles are described via the classes and associations in the upper left quadrant. The Role Activation act is used to communicate state changes (add/update/terminate) applied to the (subject) roles. Authorship of the activation acts is by the Organization entity that scopes a subject Role. For activations, the Organization is acting in its capacity as a Commissioning Party. The Commissioning Party may also i) furnish administrative 'proofs' (e.g. licenses) as primary performer of CredentialSupply events and ii) grant privileges. Commissioning party tasks may be delegated to an IssuingAgent.
The top right quadrant of the diagram models the acts associated with verifying roles in all their particulars. The collected classes in this portion of the model are still primarily placeholders for future work. The (minimal) structure in the current model shows that Verification can be the task of an independent verification agent (e.g. a Credential Verification Organization) that utilizes data from the actual role scoper or else various trusted sources as informants.
In the upper portion of the model is the Vetting class, another placeholder class that anticipates requirements for many types of observations that precede creation/activation of a role by a regulatory body (aka a Commissioning Party).
Service Delivery Location and service delivery related contact information is modeled in the bottom left corner of the diagram. This portion of the model is especially relevant to an entity playing either a HealthCareProvider or AssignedEntity role and arises from requirements to support Registry operations.
In the lower right quadrant, and linked to the RoleChoice box, are various acts for regulatory and reference information that are commonly tracked for entities playing Employee, HealthCareProvider and AssignedEntity roles. Again, these mainly arise from requirements for Registry operations.
And finally, in the upper middle portion of the diagram is a ControlActEvent with associated participations and observations. This structure is part of a complex protocol for communicating audit information and is designed primarily to support registry operations.
Entry Points and Interactions
R_Assigned Entity CMET (COCT_RM090000)
Entry point to the model is through the R_AssignedEntity role and links to the classes to support the complete description of an Assigned person, organization or device as used by the R_AssignedEntity CMET and its derivations. The committee retrofitted this CMET into the DMIM with minimum changes; however in some cases it was not possible to support the identical CMET structures as it conflicted with current tooling and methodologies. It is the committee's intention to submit change requests for this CMET in a later ballot.
E_Organization CMET (COCT_RM150000)
Entry point to the model is through the Organization Entity class and links to the classes to support the complete description of an organization as used by the E_Organization CMET. The model supports the description of Organizational hierarchies ('partof' and 'contains' roles) and contact information for a person acting as a liaison for the organization. The committee retrofitted this CMET into the DMIM with minimum changes; however in some cases it was not possible to support the identical CMET structures as it conflicted with current tooling and methodologies. It is the committee's intention to submit change requests for this CMET in a later ballot.
Human Resource (Staffing &Assignment) Interactions
Entry point to the model is through the RoleChoice box. The RMIMs for staffing and assignment messages constrain the entry point to one of two focal classes, either AssignedEntity or Employee. The playing Entity for either role supports different kinds of demographic information depending upon whether the subject is a person, organization or animal.
The focal role is scoped by an Organization entity that in turn plays the role of a Commissioning Party responsible for creation and promulgation of the particular focal Role (e.g. an organization that defines a functional role to which a person is assigned). A standard set of scoper demographics are supported; with the exception of scoper for the Citizen role and for Member role, which have unique requirements.
Interactions for managing personnel records, and for some types of registry operations, often encompass a broad spectrum of information about a person. A playing entity may have a multitude of concurrent roles, in addition to the focal one of Employee and/or AssignedEntity. These concurrent roles are 'bound together' via a RoleLink class (relatedTo) that can be seen on the model on the far right of the RoleChoice box. When serialized for a message the model permits multiple walks from the focal role to other related roles for the same playing entity as: an AssignedEntity (functional role in an organization), QualifiedEntity (education & training), HealthCareProvider (licensed practitioner), OtherLicencedEntity (licensed roles other than Provider), Employee (HR classification for payroll / remuneration purposes), Citizen or Member (of a resource group).
An example: an employed physician may hold multiple qualifications (QualifiedEntity roles), some relating to his licensed role of HealthCareProvider and some to his Employee or AssignedEntity roles. The rolelink supports differential association of these roles by binding together those that are dependent.
The current model supports only a limited set of attributes for the aforementioned Roles, their scoping entities, and the subject player. However, the list of supported attributes is increasing with each ballot cycle, as more use cases are incorporated into the domain model. Details about all of the classes can be found in the alphabetical listing at the end of this section. However, two attributes worth particular mention are present on almost all the focal roles: Role.statuscode, for communicating state changes, and Role.CertificateText to support the exchange of human readable certificates (e.g., an image of a License) or fully encoded (machine processable) certificates. (A computable form of certification data is supported elsewhere in the model, in the Vetting act).
Verification Interactions
Although still in development this model is intended to support interactions for ordering and resulting of credential verification activities. Roles represent a credentialed relationship between the scoper and player and the intent of these interactions is to ascertain the veracity of (usually) the player's claim to the competency embodied in that role.
Entry point to the model is through the VerificationRequest and thereafter to the multiple Verification acts by which the request is fulfilled. A verification request is placed in Order mood, and responded to in Promise and Event (fulfillment) moods.
Three participations are supported for the Verification events: the Subject of the activity, identified as one of the focal Roles within the role choice box; the PrimaryPerformer that carries out the verification activity, acting as an agent of a credential verification organization; and one or more Informants that substantiate the asserted competency. Informants are TrustedSource agents of either the organization that scopes the subject role or of a separate agency (e.g., a Practitioner Data Bank) that supplies evidentiary data.
The model also supports the description of Documentation (the Document act) pertinent to the individual Verification acts.
Regulatory (Role Activation) Interactions
Although still in development this model is intended to support interactions between regulatory agencies that scope roles (define and manage them) and organizations that are consumers of such information. Entry point to the model is through a focal role (in the RoleChoice box) with a walk through the subject participation to the RoleActivation control act. The latter communicates pertinent details about the regulatory activities, including state transitions of roles. Two participations are supported: the subject role, as already noted, and the author (CommissioningParty).
The author participation supports detailed information about the scoping organization in its role as the creator/manager of the Role. In both the DMIM and DAM this role is known as that of CommissioningParty.
The RoleActivation trigger event is linked to (is the outcome of) observations that precede the activation of a role. This is the Vetting act, which in this model is a 'collector' of observations: it supports communications about a person's/organization's capabilities, competencies, capacities and etc. Details are encapsulated in the .value attribute of the Act. Vetting activities may include acquiring information from external regulatory bodies. For example, the CommissioningParty is a State Licensing Board which has had the education qualifications of an applicant verified before issuing a license (a role activation) to practice as a HealthCare Provider.) To support the description of these inputs the Vetting act has a 'pertains' relationship to the Verification act and its associated classes.
Regulatory agencies are also sources of credentials and a CredentialSupplyEvent act is included in the model to communicate the issuing of certificates. This Act captures the details of the issuance of a physical or virtual token that attests to Activation of a Role. For example, a diploma (or copy thereof) attesting to the completion of university studies may be issued to a qualified recipient any number of times as requested. This Act is distinct from the original Vetting act or Role Activation.
Provider Registry Interactions
Entry point to the model is through the HealthCareProvider role, which is the focal class for interactions related to Provider Registry messages. Registry interactions use many portions of the model described in the earlier sections. Readers should refer to the class descriptions below as well the RMIMs in the Provider Topic.
Organization Registry Interactions
Entry point to the model is through the AssignedEntityRole role, which is the focal class for interactions related to Organization Registry messages. The player of this role is restricted to a PrincipalOrganization, but otherwise uses many of the same model components as the Provider Registry messages. Readers should refer to the class descriptions below as well the RMIMs in the Organization Topic.
Responsibilities & Privileges
The committee has started work on describing privileges (See Privilege and PrivilegeCategorization class descriptions) and will expand the model in future releases. Structures to support the description and verification of Responsibilities are planned fora future version of the DMIM.
Alphabetical Class ListingClasses from the DMIM are listed alphabetically within each type (Act, Entity, Role and Other - including Role Link). Associative classes (Participation, Act Relationship) are described in the context of their source and/or target and not listed separately.
Attribute comments have been included with each class description where the committee wished to supply additional clarification and/or usage notes on how the object was being employed in the domain model. The reader should interpret these comments as addenda to the RIM definition.
Roles:
-
Affiliate: Player of the Affiliate role has a business/professional relationship with scoper. Player and scoper may be persons or organization. The Affiliate relationship does not imply membership in a group, nor does it exist for resource scheduling purposes. The basis of an affiliate relationship may be a de facto agreement or simply incidental involvement of the two parties. Use case: two persons who are professional/business associates in their other roles as Healthcare providers.
Attributes:- code: coded concepts from AffilateRoleType domain.
- effectiveTime: The period in which the relationship is in effect. May be future dated.
- AlsoKnownAs: This role is indicative of an Entity (usually a person) that is known by multiple, unresolved demographics. Use case: a registry
that records an individual known to several employers by different names, DOB etc.
Usage: playing and scoping entities must have same classcode, but need not have identical attributes or values.
- Assigned Entity: This role describes an entity's functional role in an organization and is indicative of the kinds of work performed. Not
to be confused with 'Employee' role. Though often played concurrently by the same individual these roles are not synonymous.
An AssignedEntity can have a designated backup that is itself an AssignedEntity role. This is communicated via the recursive rolelink association.
An AssignedEntity role is typically identified as a component of an organization hierarchy (i.e., it appears on an Org Chart) where it is associated with some larger administrative unit. This hierarchical relationship is described via a RoleLink from AssignedEntity to OrganizationPartOf.
Attributes:- code: There is currently no a code system defined for the AssignedRoleType domain.
- addr: May be a 'positional' (role-based) address, thus irrespective of the individual playing the role.
- telecom: May be a 'positional' number, for example, the telephone number of a department manager.
- Birth Place: This role indicates a person's location of birth. It is only applicable to a Person Entity in this model. Note that Citizenship should be modeled through the Citizen Role and not derived from Birth Place. This class is optional; however, the address attribute is mandatory if the birth place is included in a message.
-
Citizen: This role describes the citizenship of a Person. The model supports multiple citizenships as business cases for this requirement have been presented to the committee.
Attributes:- certificateText: The CertificateText attribute may be used to communicate a proof of citizenship document such as a passport or citizenship card.
- Commissioning Party: This role is responsible for authoring role activations, granting privileges and supplying credentials.
Direct Authority Role Link: The Commissioning Party role is always played by an organization (for the focal roles supported in this DMIM); however, this link to the Issuing Agent Role indicates a delegated authority to a specific person, organization or device.
- Contact Party: This role and associated Person Entity describe an administrative contact for an organization.
-
Employee: This role describes the formal employment relationship from a "Human Resource" perspective and is the focal role for Human Resource messages.
Attributes:- addr: Contact information (Address, Telecom etc) is related to the employment in general and not specific to any assigned roles that are part of the employment contract.
- telecom: Contact information (Address, Telecom etc) is related to the employment in general and not specific to any assigned roles that are part of the employment contract.
-
Healthcare Provider: An entity role specific to Healthcare providers such as a Physician, Nurse or other type of caregivers. This role class is the focal role for most Provider Registry messaging. The PROV roleclass is a specialization of LIC (Licensed), which is also present on the model. Rather than having a single, specializable object in the model the committee has chosen to expose both role classes in order to better delineate any differences in usage. The model contains a textual constraint on the use of Licensed so that it is not specialized to PROV; instead, implementers are expected to use the PROV object already present in the message hmds.
Attributes:- code: Values for HealthCareProviderRoleType are derived from externally defined taxonomies of Provider types.
- certificateText: The CertificateText attribute may be used to communicate a certificate (such as a license) that is proof of the existence of this role
-
Issuing Agent: The Issuing Agent Role, linked to the Commissioning Party organization is a delegated authority responsible for authoring role activations, granting privileges and supplying credentials.
Attributes:- certificateText: attribute may be used to communicate a certificate (such as an issuing license) that is proof of the authority of this role.
- Licensed Entity: This role describes any licensed role apart from "Healthcare Provider" which is present separately on the model. (see description for HealthCareProvider). PM committee interprets 'licensed' to mean a role whose scoper has some regulatory authority over it. Thus 'licensed' is not limited to roles which carry only legal license (a license in law). Examples of licensed entities include ambulance drivers, security guards and radiology technicians.
- Member: This role describes membership in a Resource Group such as a union, professional organization or social organization.
-
Military Person: This role is a specialization of the Employee class. Proposals are pending for vocabulary specializations appropriate to military ranks and positions. Note that the committee has chosen to expose both role classes (EMP and MIL) on the model in order to better delineate any differences in usage.
Attributes:- statusCode: used to designate if the role in the military is active or inactive.
- jobCode: used to designate the military grade
- occupationCode: used to designate the occupation using the AOC, AFSC, MOS or AQD coding systems.
- Organization Contains: This role is used to describe an organizational hierarchy and is a mirror of the OrganizationPartOf role. Either or both can be used, depending upon local requirements.
- Organization Part Of: This role is used to describe an organizational hierarchy and is a mirror of the OrganizationContains role. Either or both can be used, depending upon local requirements.
-
Qualified Entity: This role describes specific qualifications that may be held by an Entity (Person, Animal or Device) as a result of training or experience, but having no legal force. Example: a medical degree or diploma.
The current model does not include role attributes such as name, addr and telecom. No known use cases in this domain where this role is 'contactable' - as, for example, is the case with AssignedEntity or Employee roles. - Role Other: This role is a component of the R_AssignedEntity CMET and was included in the DMIM because it already existed in the E_Organization CMET. It is present in the CMET to support cases in which a scoper issues multiple identifiers for a person, organization or device. These additional identifiers are not synonymous with the primary roles defined in the CMET - AssignedEntity and LicensedEntity - but may be required for record identification.
-
Service Delivery Location: The actual work location use by an entity in the role of Assigned Entity when the work location differs from the location information tracked in the Assigned Entity role or when more detail regarding the location is required.
Attributes:- effectiveTime: Time period when the SDLC is in operation.
- Territorial Authority: The DMIM contains a jurisdiction model to describe geopolitical units relevant to a focal role like that of citizen or HealthCareProvider. The domain model asserts that jurisdiction is descended: from role scoper to role player. It is a Territory-of-Authority role scoping the organization that, in its turn, scopes the role of interest. Identification of the actual geopolitical region is done via the playing entity, Jurisdiction. The model supports nested descriptions (e.g. a state territory within a country) through use of the PART rolelink, with separate playing entities (jurisdictions) for each role.
- Trusted Source: An agent role for an entity that supplies information in support of role verification activities.
- Verification Agent: This role is the person who carries out the role verification on behalf of a credential verification organization (CVO).
Acts
-
Control Act Event: This act and associated roles and observation classes are PM adaptations of a new methodology for Accountability History that slated for incorporation into Release 2 of the V3 standard.. They are used in conjunction with a proposed new attribute, ControlActReferenceId, that is (will be) a component of the HXIT datatype extension. See Modeling and Methodology paper on "HL7 UpdateMode and Accountability History" for details. When the HXIT extension is enabled for a class or attribute a string value can be entered (in a message instance) for both the ControlActReferenceId and ControlActEvent.id, thereby creating a binding between the two. Audit data relevant to the class or attribute with the HXIT extension can then be carried in the associated AssignedEntity2 and Observation classes that can be seen on the DMIM. Note that the HXIT extension is NOT visible on the graphical model, but can be enabled by a committee for incorporation into a message schema.
Attributes:- id: Identifies the data object(s) being reported upon. Note that the ControlActReferenceId that is reported in this field may have multiple occurrences in the DMIM (to support systems whose internal object model isn't RIM-based)
- Credential Supply Event: (Issuance of a Physical Token) If necessary, a Supply Act may be generated to document the issuance of a physical or virtual
'replica' of a particular credential.
Primary Performer Participation: The commissioning party organization that is responsible for actually supplying the credential.
Direct Target Participation: This is the role and associated entity for which the credential token applies.
- Disciplinary Action: The recording of a disciplinary action with respect to a subject Entity by a regulatory or authoritative body with supervisory
capacity over that entity.
Subject Participation: This is the role and associated entity that is the subject of some type of disciplinary action.
Attributes:- id: Identifier of the Disciplinary Action
- text: Free form text description of the event. Explicit typing of the kind of disciplinary action (via .code attribute) not currently supported.
- effectiveTime: Start/end dates of the disciplinary action. The period when it is in effect.
- availabilityTime: period in which information about the Disciplinary event is available for use. May be future dated. An end date in availability time indicates an archive date.
- confidentialityCode: Indicates via Confidentiality domain codes the extent to which information about the disciplinary action can be divulged.
- Inform Definition: This Act, which is in Definition mood, indicates whether or not information about the participant role is to be communicated.
For example, the participation target is the subject of a confidentiality request to support or suppress the distribution
of role-related information.
Subject Participation: this is the role and associated entity that is the subject of the Inform act.
Attributes:- negationInd: When set to 'True' indicates that information about the subject of the participation is not to be divulged. Note: the participation is optional and thus, in the absence of an explicit requirement to assert that the information can be made available, can simply be omitted in lieu of setting negationInd = "False".
- effectiveTime: time period for which the restriction is in effect.
- InformProvision: an Act describing the provision of corroborating information for a (role) Verification. The model does not include any descriptive attributes for this act, apart from identifying the performer.
-
Inform Request: A Contactable Entity (role) is the subject of a request to receive information (i.e., is the intended recipient of said information) of the type identified by this act. A separate Inform Request is required for each instance. For example, the recipient is to receive x-rays.
Attributes:- code: Describes the type of information. In theory could be almost anything, hence defaults to ActCode domain. In practice, this would typically be constrained e.g. to DocumentType.
- Note: This act supports the communication of note text attached to a particular role and the associated entity. This class is used
to communicate any free text information attached to the role that is not described elsewhere in the model. Notes are an implementation
specific business requirement, the only stipulation being that the content is intended for display or print and must be of
type String.
Subject Participation: this is the role and associated entity that is the subject of the note.
Attributes:- id: Unique identifier for the note
- text: free text
- effectiveTime: period in which the note is in effect
-
Observation Event: A component of the Audit History methodology. See ControlActEvent. Contains observed audit data in code/value pairs. One observation instance per audit attribute.
Attributes:- code: audit attribute type e.g., database dates, Registry Account Holder ID.
- value: value for the coded attribute, constrained from ANY datatype as appropriate e.g. IVL_TS for Dbdates.
- Privilege Categorization: Privilege categorization is a generic structure for providing additional information about the associated (subject) Privilege.
This is an observation act that is typed via observation.code (i.e., categories are identified by leaf level concepts in the
ActPrivilegeCategorization domain) and paired with an observation.value.
Example: a privilege to issue prescriptions may have a "Stipulation" (a kind of privilege categorization, carried in .code attribute) of "narcotics excluded" (in .value attribute).
Example: the subject privilege has a Condition upon it, that it requires a Board Approval.
Attributes:- code: identification of the kind of condition or limitation, via the PrivilegeCategorization domain.
- value: value for the category typed in code. Codified observations required, hence restricted to CD datatype.
-
Privilege: An Entity may be conferred certain Privileges that are defined against the performing Role (one of several possible focal roles in the model). Privileges, in the RIM model, are Acts in permission (PERM) or permission request (PERMQ) mood. Since any ACT could, at least in theory, be the subject of a Privilege, the Privilege clone has the simple classcode of "Act" and specification of the particular kind of Act spans the ActCode domain.
Name will be changed to Granting when GRNT type code is added to RIM.
Responsible For Participation: This is the role and associated entity that enjoys the privilege being communicated.
Participant Participation: This is the commissioning party organization that granted the privilege.
Attributes:- NegationInd: This Boolean attribute is used to indicate a negative privilege or restriction i.e., when set to True.
- text: free text description
- id: Identifier
- code: identification of the kind of privilege, via ActCode domain values.
- effectiveTime: time period in which the privilege is in effect. May be future date.
- confidentialityCode: Indicates via Confidentiality domain codes the extent to which information about the privilege can be divulged.
- Role Activation: This control act describes the establishing of a relationship (a Role) between a subject and author as well as life cycle
changes (creation, activation, termination . . .) of that Role. In the Domain Analysis Model (DAM) this is the Relationship
established between the Responsible Party and the Commissioning Party.
Subject Participation: This is the subject of the Activation act. The role-of-interest selected from the RoleChoice group (e.g. Healthcare Provider) - the DAM equivalent of Responsible Party.
Author Participation: This is the organization that created (scoped) the role in its capacity as a Commissioning Party. The Author organization is responsible for the information in the role activation.
Attributes:- reasonCode: This is the coded reason why the role activation is occurring.
- text: a textual description of the role activation.
- Verification Request: The act of requesting that a Verification Act be performed. This describes the verification processing at a global level,
as a request or promise. This is the entry point for any Verification related messaging.
Attributes:
- reasonCode: Describes the purpose of the verification - for example to validate privileges.
-
Verification: (of a Credential) An act that describes the process whereby a verifying party validates either the existence of the Role attested to by the Credential or the actual Vetting act and its details, i.e. validates the specific details (at whatever level is desired) of the original process which established the competencies, capabilities, and/or capacities that resulted in the activation of the role-of-interest.
Fulfillment Act Relationship: This relationship associates the individual verification events with the global verification request task.
Pertinent Information Act Relationship: This links the verification to documentation that supports the verification act.
Primary Performer Participation: This is the actual person who performs the verification and the organization they represent.
Support Participation: A verification act can have optional corroborating information (an InformationProvision act) supplied by a performing person, organization or device.
Subject Participation: This is the role and associated entity that is being verified.
- Vetting: (Assessment of Competency, Capability, Capacity). This is currently a placeholder class in the model. A regulatory-focused
act that collects the 'observations' about people or organization's capabilities, competencies and capacities prior to a role
being activated.
Outcome Act Relationship: This relationship links the Vetting act with the Role Activation Act. The Vetting act, at a minimum, involves the participation of the entity that will ultimately be the Responsible Party in the Activation of the Role (the subject of the Role Activation Act) as well as the participation of the commissioning party organization (the author of the Role Activation Act).
Pertinent Information Act Relationship: role verification may include scrutiny of the data that precedes activation of a role and is collected in this vetting act.
Entities
- AgentChoice: Types of entities that may play the role of agent for a commissioning party. Alternatively, one of these entities may be a trusted source of role information for role Verification activities.
- ContactPerson: This is the person who is the contact for an organization. Note that contact role does not entail the same level of responsibility as an agent. This role is also a component of the LocationLocatedEntity CMET.
- CredentialVerificationOrganization: An organization whose primary function is to verify credentials, typically on behalf of a health care employer.
- Group: A resource group. This entity is a component of the R_AssignedEntityUniversal CMET
- InformantChoice: A trusted source for role verification purposes may be either a credential agency, or the organization which scopes the role of interest.
-
Jurisdiction: The DMIM contains a jurisdiction model to describe geopolitical units relevant to a focal role like that of citizen or of a HealthCareProvider. The domain model asserts that jurisdiction is descended: from role scoper to role player. Jurisdiction is a Territory-of-Authority role scoping the organization that, in its turn, scopes the role of interest. Example: the Board having Territorial authority for the state of Maryland licenses physician to practice in that state. The Territory of Authority is played by a place (classcode =<PLC>, which in this model is the Jurisdiction clone. Code for an actual geopolitical region (state, country, province etc) is carried in Jurisdiction.code and can be constrained by specialization of Jurisdiction.classcode.
Attributes:- classcode: Specializable. In a message instance can be used to classify a jurisdiction as a State, Country etc. See EntityClassPlace domain in the RIM.
- code: Under committee review. Semantics for typing of place are already present in the classcode domain.
- Nation: This is the country to which a person may have a citizenship.
- Organization: This generic organization clone is the entity that scopes the principal (focal) roles defined in the model. Organization hierarchies are supported through the OrganizationContains and OrganizationPartOf roles. This entity is also the entry point for the E_OrganizationUniversal CMET.
- PerformerPerson: The person who performs a role verification.
- Place: a physical location playing the role of an SDLC (service delivery location).
- PrincipalChoice: Entities (person, organization, animal or device) that are the focus of the personnel management messaging and play one or more of the principal roles of interest to the domain.
Other
- Backup (RoleLink): This role link allows for the definition of one role as a backup to another role.
- Indirect Authority (RoleLink): A component of an Organizational hierarchy may have indirect authority over an assigned entity role. For example, AssignedEntity roles are created under departmental divisions or units in a hospital organization as positions in an overall hierarchy of responsibility.
- LanguageCommunication: Language use and capabilities of an entity.
- Part (RoleLink): see TerritorialAuthority
- relatedTo (RoleLink): Indicates a non-specific relationship between source and target roles. In PM domain is used to explicitly indicate a relationship
between two or more roles played by the same entity. In a message instance can also differentially associate multiple roles,
as illustrated in the following example:
A Provider Registry query response describes the history of Harold Hippocrates, currently a Physician but at one time a Registered Nurse. Along with these two HealthcareProvider roles the query results contain numerous instances of the QualifiedEntity Role, each instance corresponding to one of Harold's academic achievements. The message model must be able to associate each QualifiedEntity Role instance with the appropriate HealthCareProvider role instance, and does so by binding the roles via the relatedTo role link.
The rolelink typecode is specializable where there is a requirement to indicate a more explicit relationship. See HL7 RoleLinkType vocabulary domain value set.
Attributes:- effectiveTime: Time at which the relationship between the roles became effective, not the effective time of either of the roles involved.
| Return to top of page |